The old adage says “Don’t put all your eggs in one basket.” Yet most of us do exactly that with all of our expensive “smart” home electronics, and the consequences can be as calamitous as the old proverb implies. The latest cyber attacks are targeting home internet routers. Here’s my advice on what you need to know to defend yourself against router attacks…
Yes, Virginia, You Have a Router.
I sometimes hear from people who claim they have no router. But unless you’re on a super-slow dialup connection, you do. Some say they have just a modem they rent from their Internet Service Provider (ISP). For the record, the “modem” that Comcast and other ISPs talk about is the black box they overcharge you to rent.
That box contains the router which controls traffic on your home network as well as the modem that handles communication with the Internet. So yes, this article is relevant to you, too.
The “basket” I mentioned in the intro is your home’s router, the device that acts as a gateway between the Internet and all the gadgets in your home that use it. When malware compromises your router, it’s as if a fox pried open your basket of precious eggs. Everything on your home network is compromised, too.

That is one reason to run anti-malware software on each computer attached to your home network even though the router may have a firewall or other security features designed to keep intruders and malware out. If the router’s protection fails, individual devices may save themselves. The performance hit imposed by such redundancy is negligible compared to the potential risk to computers that harbor irreplaceable data. An even greater reason not to rely on your router’s security is that it is almost non-existent, in most cases.
The firmware of most consumer-grade routers is poorly written to begin with, is often left unpatched when vulnerabilities are discovered, and almost certainly will not be supported longer than two years after your particular router make/model was released. (How long have you had your router? How old was it when you got it?)
This disgraceful state of affairs is especially true for cheap, no-name routers. Brands that I consider trustworthy include TP-Link, Netgear, Linksys, ASUS, and D-Link. If you see a router advertised on Amazon, but it’s a brand you’ve never heard of, and yet somehow they’ve got thousands of glowing reviews, put down the mouse and back away slowly.
Consumer-grade routers are commodities differentiated only by price in the minds of most buyers, who do not grasp the technical mysteries of these boxes that “just sit there blinking.” Consequently, manufacturers shave their costs in every possible way. Software quality and support are sacrificed heavily.
Signs Your Router May Have Weak Security
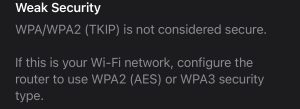
You may have noticed that your router does not automatically update its software; that updates are never trumpeted via the trade press; that it is devilishly difficult to find current router software on manufacturers’ sites, and tricky to install it correctly if you do find the right update. Even basic documentation of the software that ships with a router is often terribly slim and reads as if was run twice through Google Translate. These are all signs that a router maker has skimped on security software and support.
Another sign of weak security is that the only advice you get for improving security is, “Change the default admin password.” That is the first thing you should do with a new router; if it is the last thing you can do, the router still may have no meaningful security.
“Disable remote administration” is another router security recommendation that should be implemented but does not hacker-proof your router. Remote administration allows you, your ISP, and possibly some hacker in Romania the ability to login to the router via the Internet. Hackers have known about “cross-site request forgery (CSRF) ” tricks that get around this safeguard for many years, but some cheap routers still don’t close this hole.
Your ISP may not even allow you to disable remote router administration. After all, it makes their job a lot easier if they have to reconfigure your router. This is a case of “better to ask forgiveness than permission.” Disable remote administration if you can; address any objections from your ISP only if necessary.
You have the legal right to use your own equipment on your side of the ISP’s box as long as it doesn’t interfere with anyone else’s service, according to the FCC and well-settled case law.
Protecting the IP addresses of the DNS servers that your router uses to look up Internet sites is another security essential that cheap routers neglect. These DNS server IP addresses are stored in the router’s memory. A badly secured router leaves it vulnerable to “DNS hijacking” in which requests for domain name lookups are misdirected to an attacker’s bogus DNS server, and what you see in your browser’s address bar may not be the site that you think it is.
If your home network’s security is worth $100 to $150 amortized over five years, then you should be willing to buy a better router, too. If you are paying for malware protection of individual devices on your home network, a competent router makes that investment more worthwhile; otherwise, you are sacrificing the redundancy that makes security as good as it can be. Check out the Asus RT-AC5300 router, Netgear’s Nighthawk AC1900 family, and models in the Linksys “Smart Wi-Fi” family of routers.
What You Can Do For Free
That said, here are some things you can do to configure better security on any router. I cannot provide detailed instructions for your specific router; but in most cases you’ll start by connecting to your router via this address: http://192.168.1.1 and providing the admin username and password. If you need help logging into your router, or changing the settings once logged in, contact your ISP or look for instructions online.
Your first task is to change the administrator’s password; this one cannot be repeated often enough. Many routers ship with a default password, or no password at all, leaving them wide open to attack.
Disable remote administration: discussed above. The router should be accessible only via a physical Ethernet cable, or from a specific, fixed IP address of a device designated for the administration of the router (such as the owner’s PC or phone).,
Change the router’s IP address. Hackers typically look for vulnerable routers at a factory-default IP address like 192.168.1.1; if that fails, the attack fails in all but the most sophisticated campaigns. But there is no reason a router can’t have another IP address, and your router’s administration interface should allow you to make such a change.
For example, you could choose 192.168.0.100 as your router’s IP address. Log in to the router’s administrative interface in the usual way, via the default IP address. Navigate to the page that enables changes to the router’s IP address and make your change. Save changes and reboot the router. Henceforth, enter the router’s new IP address in your browser’s address bar to access the router’s admin interface.
Keep router firmware up to date. Automatic updating of router firmware should be as standard as automatic Windows Update on all routers; don’t buy a new router without it. Newer models from Linksys and Netgear include automatic firmware updates as an option.
Changing the router’s default password is the first, easy step towards router security you can count on. If you also perform any one of these reinforcements to your router’s security, you will have thwarted a significant portion of other potential attacks. Implement all of these suggestions if you can.
Have a great week from all of us at Zoha Islands And Fruit Islands
