We post these tech articles to inform Second Life users of the way accounts get hacked and how to avoid major problem’s in the future from attacks within the viewer (which is not as secure as we think) So please read on and secure your computer don’t let this happen to you!
Ransomware seems to be the darling of bad guys these days. It’s a very direct, powerful technique for extorting hundreds of dollars from a single victim very quickly, or millions of dollars when there are thousands of victims. Let’s take a look at the latest ransomware campaigns and how you can protect yourself from them… Recent account hacks in second life have not only locked people out of their accounts but have wiped out all L$ as well as attached ransomware to computer.
Ransomware: Detection and Protection
For anyone unfamiliar with it, ransomware is a type of malware that denies a victim access to his or her computer by locking its screen and/or encrypting the files on the hard drive. When a victim tries to access the computer, all they get is an ominous screen like the one below, that says “Oops, your files have been encrypted!”
The essence of the deal is, “Pay $X within Y days or you’ll never see your data again.” It’s extortion, pure and simple. But ransomware is getting much more sophisticated these days. The screenshot below comes from the Wannacry ransomware, which infected hundreds of thousand of computers in a single weekend in May.
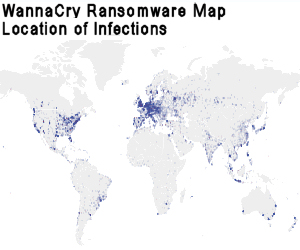
The map shown here was generated by IBM, and shows the worldwide distribution of Wannacry ransomware infections. Apparently, you’re safe if you live in Papua New Guinea, Greenland, Niger or Chad. The rest of the world, not so much.
 Payment in Bitcoin, the digital crypto-currency, is required. Most victims don’t know much about Bitcoin, so Wannacry and other recent ransomware provide surprisingly good “customer support” to guide victims through the process of creating a Bitcoin account, funding it with real money, and sending money to the extortionist.
Payment in Bitcoin, the digital crypto-currency, is required. Most victims don’t know much about Bitcoin, so Wannacry and other recent ransomware provide surprisingly good “customer support” to guide victims through the process of creating a Bitcoin account, funding it with real money, and sending money to the extortionist.
One characteristic of Bitcoin is transparency; anyone who knows how can view all Bitcoin transactions since Bitcoin was created. Experts who have examined Bitcoin payments to the creators of Wannacry estimate that this global act of terrorism has so far generated only about $92,000 for its perpetrators. That’s a small return on the infection of an estimated 200,000 computers in 150 countries.
It turns out that Wannacry has a “kill switch” embedded in it that can halt the spread of Wannacry in its track. Within Wannacry’s code is a routine that constantly checks a gibberish domain name to see if it has been registered. As long as the domain remained unregistered, Wannacry would continue infecting any computer it could reach. But when a 22-year-old British security analyst who goes by the handle “MalwareTech” registered that domain, Wannacry stopped trying to spread itself. Amazingly, it cost only $10.69 (the domain registration fee) to halt this worldwide scourge.
That still left hundreds of thousand of computers infected by Wannacry. It’s a mystery how most of them, apparently, have either eradicated the infection somehow or are managing to get by without their data and computers. The UK’s National Health Service is still dealing with the fallout of widespread Wannacry infections on its network, delaying elective surgeries and slowing the nation’s entire health care system to a crawl.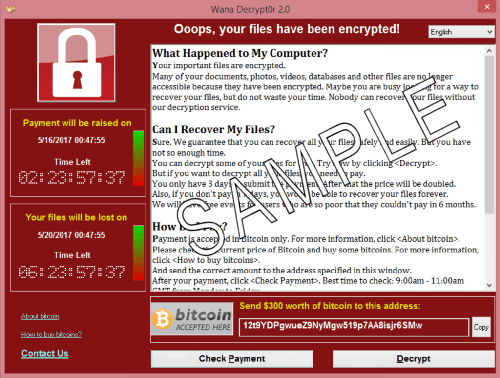
Other Ransomware Attack Vectors
If you have been infected by ransomware, don’t run off and buy a bucket of bitcoins. First check in with the No More Ransomware Project, which offers free decryption tools for a range of ransomware attacks.
Another new form of ransomware has been dubbed “doxware.” You are unlikely to encounter it because it’s a technique that requires a lot of legwork from the perpetrators. First, they identify high-value targets, computer networks that house highly sensitive, confidential data. Then they infiltrate those networks with ransomware that not only encrypts all files, but also sends to the perpetrators select files that contain words like “confidential,” “top secret,” and so on. Then the victim is told that these files will be posted on a public Web site and all of his contacts will receive the URL that links to that site, unless he pays up by a specified date.
The best defense you can mount against ransomware, or any kind of malware infection, is to keep your operating system up to date with patches for all known vulnerabilities. If you allow Windows Update to run automatically, you should have received the patch to protect against the latest threats.
Microsoft even released a Wannacry patch for Windows XP and Windows 2003, obsolete operating systems that officially no longer receive security updates. Many computers in China, Russia, and even the USA are still running XP, despite its ever-growing vulnerability to hackers and malware. See Microsoft’s Customer Guidance for WannaCrypt attacks to read the company’s response to WannaCry, and links to those patches.
Trust No One
Other good advice here includes “Trust no one. Literally.” Do not click on any link or file attachment – even if it seems to have been sent by your bank, your brother the IT administrator, or your Mom – until you know what you are clicking on. If a message seems out of the ordinary, call your contact and ask if he or she sent it. No account is safe from hacking or impersonation (“spoofing”).
For further protection, enable the ‘Show file extensions’ option in the Windows settings on your computer. To do so, type “folder options” in the Start menu’s search box and click on “Folder Options” in the search results. In the dialogue window that opens, select the “View” tab. Uncheck the box next to “Hide extensions for known file types”. Click “OK” to save this change and close the dialogue window.
The purpose of showing common file extensions is to help you spot executable files (programs) that are disguised as non-executables. With “hide extensions” enabled, a file named WatchMe.avi looks like a video file. But with all extensions revealed, it may be WatchMe.avi.EXE and that is a big red flag. If you see multiple file extensions, delete the file without opening it.
A good anti-malware suite is also essential, and it must be kept updated too. I use the combination of Avast anti virushttp://avast.com/ and Malwarebytes Antimalware (MBAM) to provide double coverage.
And of course, be ever-vigilant about opening email attachments. When in doubt, contact the sender to ensure that they actually sent it, and that it’s safe to open.
Have a Great Week
Deuce Marjeta
