Once more, Bob Rankin’s blog “Ask Bob Rankin” alerts us to a recent outbreak of a ransomware malware called “Cryptowall 2.”
Bob goes on to say that “Making regular backups of critical data and keeping your software up to date is more important than ever thanks to the arrival of new, “improved” malware like Cryptowall 2. This update to a well-known ransomware exploit is making life miserable for business and personal computer users worldwide.”
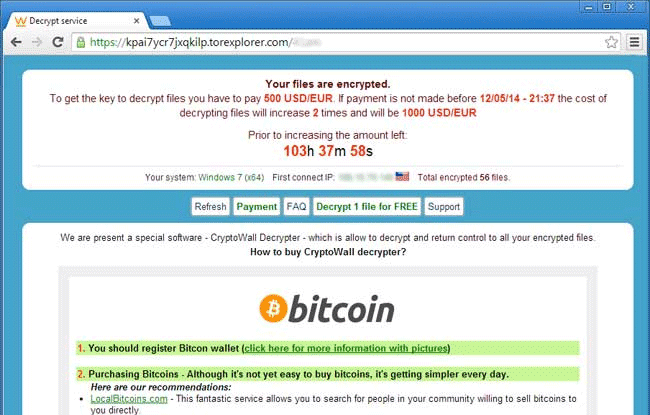
Cryptowall 2 is a variant of the CryptoLocker virus, which was created and launched last summer by cybercriminals, and the authorities were able to successfully shut down that threat. However, this new Cryptowall 2 is out there and is dangerous.
Bob states “Like its predecessor, Cryptowall 2 encrypts everything on an infected hard drive and displays a “ransom note” to the hapless user. The extortion is simple: pay several hundred dollars by a specified deadline or you’ll never get the key that unlocks your encrypted data. The payment method is anything but simple for the typical victim.
“Cryptowall 2 is elaborately designed to avoid detection by security software and to conceal the identities and locations of its masters. Part of this stealth strategy is to require ransom payment in Bitcoin, the virtual crypto-currency. Most citizens and even IT geeks have no clue how to get Bitcoin; even if you know, converting real currency into Bitcoin is not convenient or fast.”
Bob goes on to say that “As if that isn’t enough, a Cryptowall 3 version appeared in recent days. Its only “improvement” seems to be the addition of the Invisible Internet Project (I2P) proxy network to the things that can go wrong with a payment attempt. The payment link provided by Cryptowall runs a victim through several Tor proxies and then hands the connection off to I2P, which has its own ways of failing.”
We cannot emphasize enough how critical it is to back up your data regularly, and to be very cautious about clicking on links or opening emails from unknown sources. The best way to deal with Cryptowall is to avoid it at all costs. That means keeping your defenses up on all fronts. Think before you click on unknown links or email attachments. Keep your operating system and application software up to date with security patches. Use a comprehensive internet security suite that watches for things like Cryptowall in email, Web, external storage devices, and every other vector by which malware can enter your system.
Bob recommends these links to learn how and where you can get free tools to protect your computer:
He also recommends an extra layer of protection using a program called CryptoPrevent, which modifies some Windows settings to prevent infection by Cryptolocker and related malware. Note that there are both Free and Premium versions of CryptoPrevent.
You can see the entire blog post on Bob’s blog here: Ransomware Strikes Again.
I remain respectfully yours,
~ Suzanne Piers, ZI Social Media

