Hello to all at ZoHa Islands – lets talk about paranoid! Here are 10 tips to stay secure in Second life and all around in general on the Internet.
They’re watching you. Literally. In a recent article posted at Ars Technia, it was reported that hackers have the ability to remotely take over your computer and install software on your computer that allows them to turn on your webcam. What? They do this using a RAT pack (Remote Administration Tool). In addition to that, we are hearing of new router exploits that give a hacker the ability to remotely access your router and gain access to your Local Area Network. If you think you’re overly paranoid about your computing you should be. This stuff is scary.
So now that you know that the whole world is out to get you, what can you do about it? These steps will help close some of the holes used to exploit computers.
Turn off Remote Administration – Remote administration in routers give users outside of your network the ability to access and control your router. In many cases, this is turned on by default. What? Of course the intention of this option is benign, but it can be used by a hacker to get into your LAN and see all of your internal computers, manipulate your firewall and do basically anything they want with your traffic.
To do this, you can navigate to your router’s admin page using your web browser. Normally, this can be done by typing http://192.168.1.1 or http://192.168.0.1 into your browser’s address bar (not the search bar). Your router location may vary. You will also need to know the username and password of your router. If you do not know it, and the router was supplied by your ISP, you can check the physical device to see if the information is printed there or call your ISP for log in details.
Look for an “Advanced” or “Administrator” tab and make sure remote administration is disabled.
Turn Off Wake On LAN – While not necessarily an exploit, WoL allows your computer to be turned on when powered off from an outside source. Imagine this, ole paranoid one, if a hacker had access to your internal LAN and had the ability to turn on your PC whenever he or she wanted to perform whatever nefarious acts he or she wanted. Unless you have a specific need to have it on, go into your computer BIOS when booting and disable that wicked feature. Depending on your BIOS, it may not even be an option.
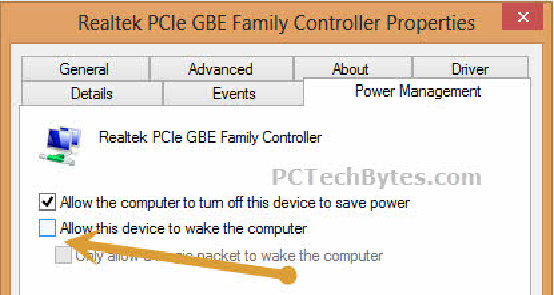
Turn Off Allow Network Traffic To Wake Computer – Similar to WoL, your network adapter has the ability to listen to network traffic and can allow your computer to be woken up while asleep.
To shut this down, go into the Control Panel, look for your network adapter, right-click it and select Properties. Under the Power Management tab, uncheck that option if it is checked.
Turn Off UPnP – Turn off Universal Plug and Play in your router. Universal Plug and Play allows programs within your network to automatically punch holes in your router. What? Us paranoids can’t allow this to happen! Imagine a virus on your network having free reign to open ports on your router to allow even more bad guys in. For most of us, having this feature off will not affect anything we do from day to day. For others, you may need to occasionally go into your router and manually open ports for programs or system that require them to be open–like game consoles, for instance. You can turn off UPnP in your router.
Uninstall Java and Adobe Reader – With Windows doing a better job securing the OS, hackers are seeking softer targets like Java and Adobe Reader, both of which seem to have some type of zero-day exploit a couple times a year. Most of us have these programs just sitting on our system, never being used and never being updated to the latest versions. If you simply must have them, be sure to update them frequently.
Scan Your Ports – The Gibson Research Corporation (GRC) has been providing a free online tool to scan your router for open ports for over ten years. This tool is called Shields Up and you can find it here. The UPnP Exposure test will check to see if your router is open to a new router exploit that gives hackers the ability to access and control your router.
If all is well with the GRC test, you will see the above image.
Run Your Browser In Privacy Mode – Private Browsing (which may be called something else depending on which browser you’re running) allows you to surf without the fear of a history being saved, and temp images, videos, files and cookies being stored on your computer.
In Firefox and IE, this is enabled by hitting CTRL+Shift+P.
In Google Chrome hit CTRL+Shift+N for Incognito mode.
Do The Basic Computer Security Measures – Of course, you should also make sure you are running a current antivirus–if your free antivirus from Symantec or Mcafee has expired, uninstall it and get another. If you do not have one, Microsoft Security Essentials is free. In addition, make sure your WiFi is encrypted in your router settings using WPA-2 so the whole neighborhood isn’t using your bandwidth. Make sure you have Windows automatic updates turned on. Make sure your Windows firewall is also enabled. Modern Windows Operating System will have these on by default, and if you’re running Windows 8 you also already have an antivirus called Windows Defender–built in.
Using general account: you should always run as a standard user. The theory is, if you happen to get malware on your system, the malware will not have the elevated rights of an admin because it is running under an account that only has standard rights. While this won’t necessarily protect you completely, it is one more thing you can do to slow down the bad guys. Keep your admin account, of course, because you will occasionally need it to install software, etc.
Use WAP-PSK encryption instead of WEP
WEP is like locking your house with a screen door.
Thanks for reading have a great week…
Deuce Marjeta
Operations Manager